Use the "ssh -D" command to encrypt web surfing on an unprotected network
Sometimes you may be surfing on a network that is insecure because people can listen in. This could be the case if you're on an unencrypted wireless network. If you have access via ssh to a server somewhere, you can log in to that server:
ssh -D 12235 username@server.somewhere
The -D switch to ssh will make ssh work as a SOCKS proxy server and the traffic will be sent encrypted to your server (and then as plain http from there).
In your web browser you need to configure it to use a SOCKS proxy and the port number 12235 (I just made that port number up, you can use another one as long as you use the same number after the -D switch to ssh and the port number you put into the proxy configuration of your browser).
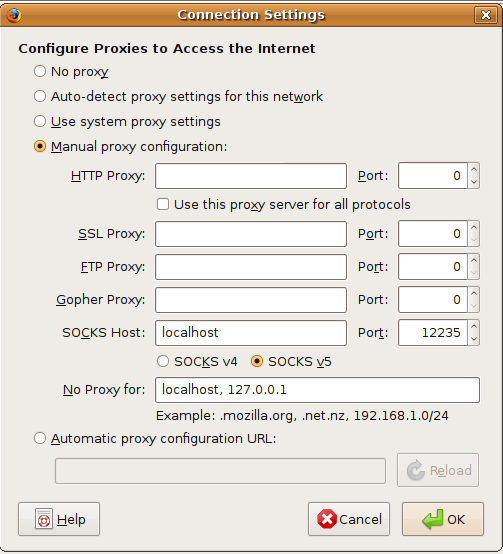
Settings in Firefox 3 on Ubuntu Linux 9.04
In order to check the connection you can use a service such as whatismyipaddress.com and check where it thinks you are.
Now, http traffic will still be eavesdroppable from your server and onwards. For https (SSL) addresses you don't need to encrypt it because it already is, but the above solution should hide what server you are connecting to.
For a solution with a dedicated proxy server and separation of http and https traffic take a look at this blog post.
I got the hint for the -D switch from here:
I was able to send my Google Talk traffic encrypted through the firewall back to my server at home and then out to Google. All I had to do was reconfigure my Jabber client to use localhost as the server and the port 3000 that I had configured.
Read more: HOWTO: SSH Tunneling Made Easy